Support Page Content
Data Security & Records Retention
CSU Information Security Policy and Standards and EO-1031 Records Retention Policy requires that Sacramento State delegates administrative authority and responsibility to appropriate campus administrators charged with granting access and ensuring appropriate controls are in place to protect campus information assets.
The following five distinct governing bodies are responsible for helping to create and approve policies and procedures that support data security and data‐driven decision‐making:
- Data Governance Executive Council
- Data Owners Group
- Records Management Working Group
- Data Reporting Governance Working Group
- Computer Security Incident Response Team (CSIRT)
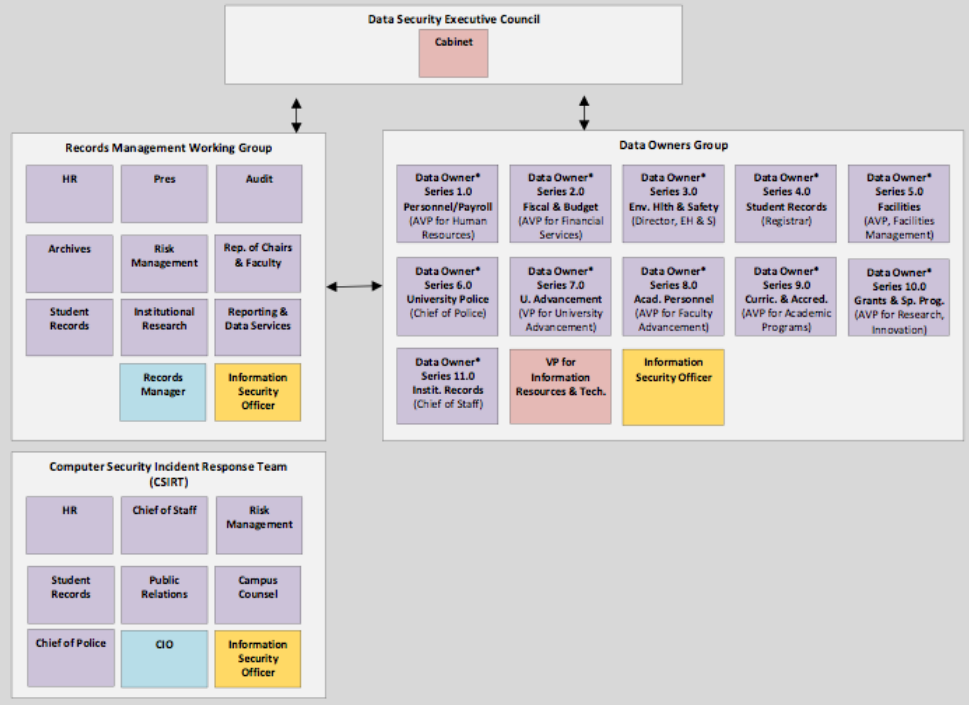
Data Governance Executive Council
Membership: Cabinet members
Purpose: To provide executive level guidance to the program, and:
- Review deliverables from the Records Management Working Group and Data Owners Group, make decisions, and communicate decisions to the groups and campus.
- Review and guide the priorities of the Records Management and Data Owner groups.
- Consider requests for resources when needed.
- Ensure that major data security initiatives align with the University’s strategic goals.
- Formally designate and delegate official Data Owners for data records within their purview. (If a Data Executive does not formally designate a Data Owner for a particular data series, the Data Executive retains Data Owner responsibilities).
Data Security Executive Council (Cabinet) Operations
- Responsibilities can be conducted during regularly scheduled Cabinet meetings. Agenda items will be submitted to the President’s Office via a Cabinet member.
Data Owners Group
The Data Owners Group consists of senior campus administrators who play a primary leadership role in ensuring the confidentiality and security of University data. They have policy‐level managerial responsibility for data within their functional areas, and are supported by a select group of information technology managers with data-related roles. Data Owners must have a formal designation or delegation from their Vice President/Cabinet member. This group will focus primarily on compliance and security issues, and will:
- Grant access to data and ensure appropriate controls are in place to protect information assets based on ISO Domain 9: Access Control Policy and ISO Domain 8: Asset Management Policy
- Classify data, define controls, authorize access, monitor compliance with campus security policies and standards, and specify levels of acceptable risk.
- Ensure development of appropriate role‐based or attribute‐based permissions and employment groups that allow appropriate access to be granted efficiently.
- Review and approve enterprise system security roles that define how appropriate access is provided to set(s) of data.
- Ensure that access to records is reviewed and/or removed when an individual with access is transferred to a different position/department on campus, or when separated from campus.
- Oversee records retention and disposition processes. The Data Owner is the campus-designated department head who maintains the official/original copy of the record/information series for retention purposes in compliance with EO 1031 Records Retention Policy. Please refer to the CSU Records Retention and Disposition Schedules.
- Identify business units and systems that are not compliant with CSU records retention requirements, and ensure that those units/systems are aware of their non‐compliance.
- Comply with CSU and University data classification and protection standards.
- Ensure that the biennial Sensitive Data Inventory Survey is completed by all units within their responsibility.
- Contribute to the development/delivery of a campus security and awareness training program.
- Designate official Data Managers for specific data sets within their purview. If a Data Owner does not designate a Data Manager for one or more data sets, the Data Owner retains Data Manager responsibilities.
- Draft and recommend policies and standards to Cabinet.
- Recommend campus data improvements and provide input to the Records Management Working Group to inform program documentation.
- Review and discuss compliance and security issues to ensure that they are reasonably and consistently addressed within the University's information security technical and business guidelines, standards, and processes.
Data Owners Group Operations
- Meets quarterly, at minimum.
| Schedule Series | Schedule Series Data Owner Title | Member |
|---|---|---|
| 1.0 HR Personnel/Payroll (rev. 8-24-2022) | Senior AVP for Human Resources | Machelle Martin |
| 1.4, 1.5, 1.17 HR Personnel (rev. 8-24-2022) | Vice President for Inclusive Excellence | Michael Nguyen |
| 2.0 Fiscal (rev. 3-13-2023) | Associate Vice President for Financial Services | Gina Curry |
| 3.0 Environmental Health & Safety (rev. 2-26-2020) | Director of Environmental Health & Safety | Tyler Harris |
| 4.0 Student Records (rev. 5-19-2021) | Associate Vice President for Student Services and Enrollment Management Systems | Tara Hardee-Teodoro |
| 4.3 Financial Aid (rev. 5-19-2021) | Director of Financial Aid and & Scholarships | Tina Lent |
| 4.1.8, 4.5.3, 4.7.1, & 4.7.2 Student Health Records (rev. 5-19-2021) | Senior Associate Vice President for Student Health and Counseling Services | Jeanne Harris Van Dahlen |
| 5.0 Facilities (rev. 3-15-2023) | Associate Vice President for Facilities Management | Felicia Johnson |
| 6.0 University Police (rev. 3-17-2023) | Chief of Police | Chet Madison |
| 7.0 University Advancement (rev.6-17-2019) | Assistant Vice President for Advancement & Prospect Engagement | Sharise Harrison |
| 8.0 Academic Personnel (rev. 8-26-2019) | Vice Provost for Faculty Success | Rebecca Cameron |
| 9.0 Curriculum & Accreditation (rev. 6-19-2019) | Associate Vice President for Academic Excellence | Amy Wallace |
| 10.0 Research & Sponsored Programs (rev. 7-23-2019) | Associate Vice President for Research, Innovation and Economic Development | Lisa Hammersley |
| 11.0 Institutional Records (rev. 2-3-2021) | Chief of Staff | Kristen Tudor |
Records Management Working Group
Membership: Data owners, managers, and consumers, and IT managers
Purpose:
- Help interpret and administer policies.
- Create and maintain program documentation.
- Recommend appropriate resources (staff, technical infrastructure, etc.) and ensure that proper planning protocols are in place to support the data security and retention needs of the University.
- Advocate and promote data stewardship across the University.
- Contribute to the development/delivery of a campus security awareness and training program.
Records Management Working Group Operations
- The group will meet bi‐monthly at minimum.
- A quorum is met if three quarters of the members are present.
- Formal recommendations to Cabinet and/or updates to the program documentation need to be ratified by a quorum.
- Minutes will be taken for each meeting and will be approved at the next meeting.
| Position | Member |
|---|---|
| Archives | Vacant |
| Audit | Vacant |
| HR | Machelle Martin |
| Information Security Officer (CISO) | Nathan Zierfuss-Hubbard |
| Institutional Research | Vacant |
| President | Vacant |
| Records Manager | Vacant |
| Reporting & Data Services | Greg Porter, interim |
| Rep. of Chairs & Faculty | Vacant |
| Risk Management | Todd Dangott |
| Student Records | Vacant |
Data Managers
Data Managers oversee and support the day‐to‐day business processes used to maintain University data. Data Managers are typically considered subject matter experts on specific sets of data elements, and understand how data is used by Data Consumers. Data Managers are often designated by, and have an organizational reporting relationship to, Data Owners, and will:
- Comply with University and CSU policies and follow established business processes for data handling and records retention and disposition responsibilities for records in their care. Refer to the CSU Records Retention and Disposition Schedules and CSU EO 1031.
- Identify business units and systems that are not compliant with CSU records retention requirements and ensure that those units/systems are aware of their non‐compliance (in coordination with Data Owners when appropriate).
- Ensure that the Biennial Sensitive Data Inventory Survey is completed by all units under their responsibility (in coordination with Data Owners when appropriate).
Data Consumers
Data Consumers include the individuals, organizational units, and information systems that are granted access to data for specific uses such as analysis and reporting. This designation can also include downstream information systems that ingest and/or transform data for a specific purpose.
Data Consumers
- Provide input to Records Managers and/or Data Owners about data management and security needs.
- Review data security and management reports for the purpose of data‐driven decision‐making.
- Identify and report data quality issues.
- Attend training to clearly understand their data responsibilities, and follow procedures to ensure data security.
Data Authorization
Sacramento State utilizes a number of applications and systems that store, use and/or transmit data. This data may include confidential, sensitive and/or need to know information. Per CSU policy access to this data is granted only after the required vetting, approvals and the completion of the CSU Systemwide Data Security Privacy and FERPA training.
In addition to user access there are implementations that may require the transmission of data between systems and/or to other data repositories and exchanges. These are usually accomplished through application interfaces and other mechanisms developed by functional and technical personnel.
To ensure that university data is safeguarded and shared appropriately when necessary, the Data Authorization Request/Approval process is required. This must be completed prior to developing/implementing the logistics to extract and/or import data from/to the source or destination systems. All data requests should be entered on behalf of the Data Manager and approved by their respective supervisor and then the appropriate Data Owner.
For questions and/or assistance to submit Data Authorizations requests please contact the Information Security Office (iso@csus.edu) or the Project Management Office (itprojects@csus.edu) in IRT.
Computer Security Incident Response Team (CSIRT)
The Computer Security Incident Response Team (CSIRT) is a subgroup of the campus Critical Response Team charged with evaluating potential security incidents and breaches to provide recommendations to the President.
- CSIRT group works closely with the Chancellor’s Office, University Police, Campus Counsel, and with the IRT Information Security Office (ISO) during potential breaches to evaluate technical and administrative components, including breach containment and notification requirements.
- The ISO provides the committee periodic reports concerning significant security incidents and overall institutional risks and vulnerabilities.
Meeting Schedule
Meets periodically throughout the year for proactive tasks such as Disaster Recovery and Incident Response testing, and/or as-needed in the event of a security breach.
| Position | Member |
|---|---|
| Campus Counsel | Sasha Danna |
| Chief of Police | Chet Madison |
| Chief of Staff | Kristen Tudor |
| CIO | Mark Hendricks |
| HR | Machelle Martin |
| Information Security Officer (CISO) | Nathan Zierfuss-Hubbard |
| System-wide CISO | Josh Callahan |
| Public Relations | Jeannie Wong |
| Risk Management | Gary Rosenblum |
| Student Records | Brian Henley |